A new method of avoiding detection
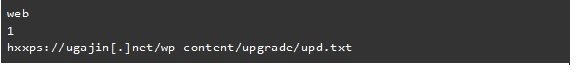
Paradise ransomware was active since 2017 but as a regular ransomware group. Attackers behind it are now trying new methods to mark themselves unique. And this is by leveraging IQY or Internet Query Files. These are text files used by Microsoft Excel to procure data from the internet. It contains URLs and other parameters to make queries on the internet. Since these files are legitimately used by Excel, they won’t be flagged malicious by any antivirus softwares or special detectors. And as companies exchange Excel sheets within and out often, there are high chances of these malicious IQYs spreading. Paradise ransomware, like every other ransomware attacker, operates phishing campaigns against targeted corporates to gain network access. They send malicious emails with these IQY files to be clicked by employees. And once this happened, the IQY file contacts and connects to attacker’s C2C server that in return sends a Powershell script. This finally executes the ransomware within the system by encrypting all the data.
Just trailing yet, could be worse in future
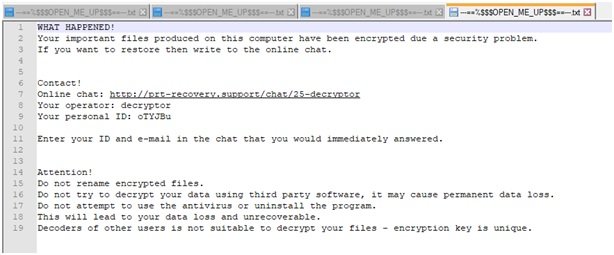
After being done with encryption of the whole network, it leaves a ransom note where it mentions instructions to be contacted. Lastline Threat Intelligence, the team which surfaced this operation has contacted the ransomware attacker via a chat support option to know more. But the author didn’t respond to it yet. This indicates the attackers are more interested in knowing the campaign’s success rate rather than just ransom. This could be speculated for more severe attacks in the future. Usage of IQY files in its operation describes Paradise ransomware too is targeting companies rather than individuals, as the former garner lump sums rather than later tidbits. Best way to safeguard against such attacks is to maintain an updated backup offline. If not, proactively suspecting the links or attachments coming with malicious emails in the first place. This would help avoid such bummers. Source: Lastline