The Dangerous Botnet Malware Has Risen Again
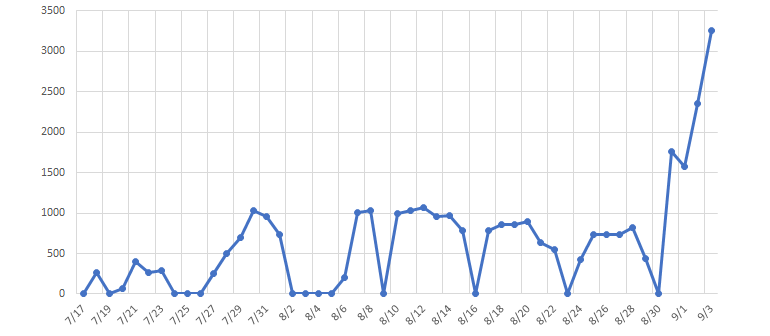
Emotet gang has been a sophisticated botnet network that leverages weak situations like COVID-19 and activates suddenly. Like a hit-and-run case, it sometimes set no specific targets to send malicious emails, but rather send in bulk to capture any leads. It works by sending a malicious attachment, and install its backdoor when opened by the user. Upon setting a backdoor, it would then invite other trojans like TrickBot, or ransomware attackers like Ryuk or Maze to infect further and steal data. It’s found being so active in February this year, where it sent hundreds of thousands of emails every day to employees of companies all over the world. Later, in July targeting companies in the US and UK especially. And now, it’s heavily targeting companies in Japan, France and New Zealand, which made cybersecurity agencies of those three countries to issue a security alert to their domestic corps to be vigilant. They have listed the signs of being hacked and what to do if compromised. Especially the Japan and New Zealand have been heavily targeted than that of France, which has seen a sharp spike in Emotet attacks. To make itself more attractive to open, Emotet gang first target a victim and steal his latest e-mail threads. These would later be used to craft the following email to that, along with its malicious attachment and joins to original email thread of target to be opened easily. Cybersecurity agencies warn companies to check before opening any suspicious emails and disconnected all systems and inspect them individually in case compromised.