Fallen into a Honeypot!
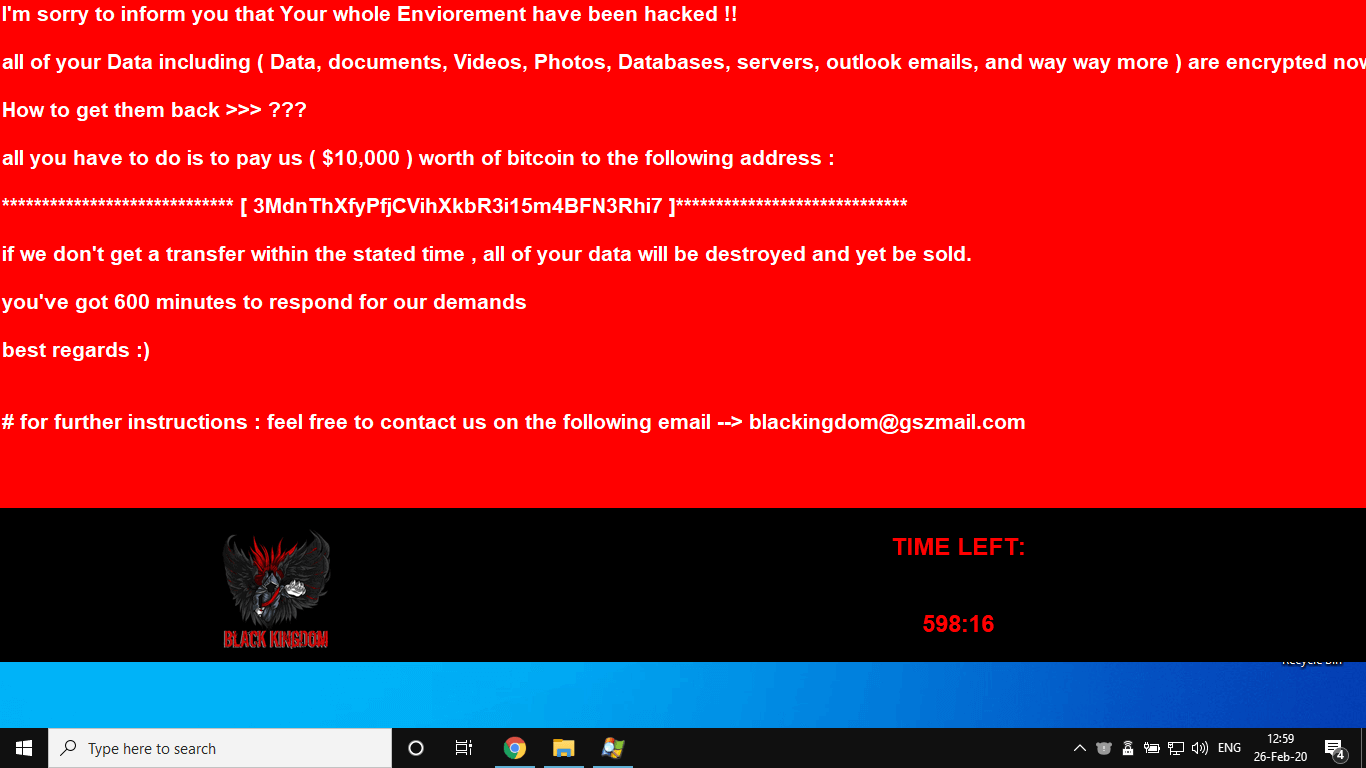
As REDTEAM.PL group discovered, the Black Kingdom ransomware has been exploiting a known vulnerability (CVE-2019-11510) in Pulse Secure VPNs, which was disclosed last year. US government has warned about this attack multiple times since then. Yet, many organizations using this VPN haven’t applied the available patch, thus vulnerable to attack. As researchers said, this ransomware group is gaining access into the network by impersonating the legitimate tool scheduled task in Google Chrome, which runs on the Base64-encoded string code. This was available in a hidden PowerShell window that procures a script called “reverse.ps1” which is used to open a reverse shell on the victim’s machine. Upon tracking the script reverse.ps1, the IP address storing it was detailed as 198.13.49.179, which is hosted by Choopa, a cheap VPS provider popular among cybercriminals. Further examination reveals that there are three domains as host.cutestboty.com, keepass.cutestboty.com, and anno1119.com linked to that IP address, where the third domain of that is connected to servers Italy and US. And these domains are housing cryptocurrency mining and Android malware! As samples found in REDTEAM.PL’s report, contacting the IP address showed a ransomware note, that asked for a $10,000 in Bitcoin to be deposited in a stipulated time, else the data stolen from PC/network will be sold and destroyed. Further check into the given Bitcoin address revealed no funds in the wallet, but a 0.55 Bitcoin incoming or in process. Via: BleepingComputer