Phishing – Dumping – Execution
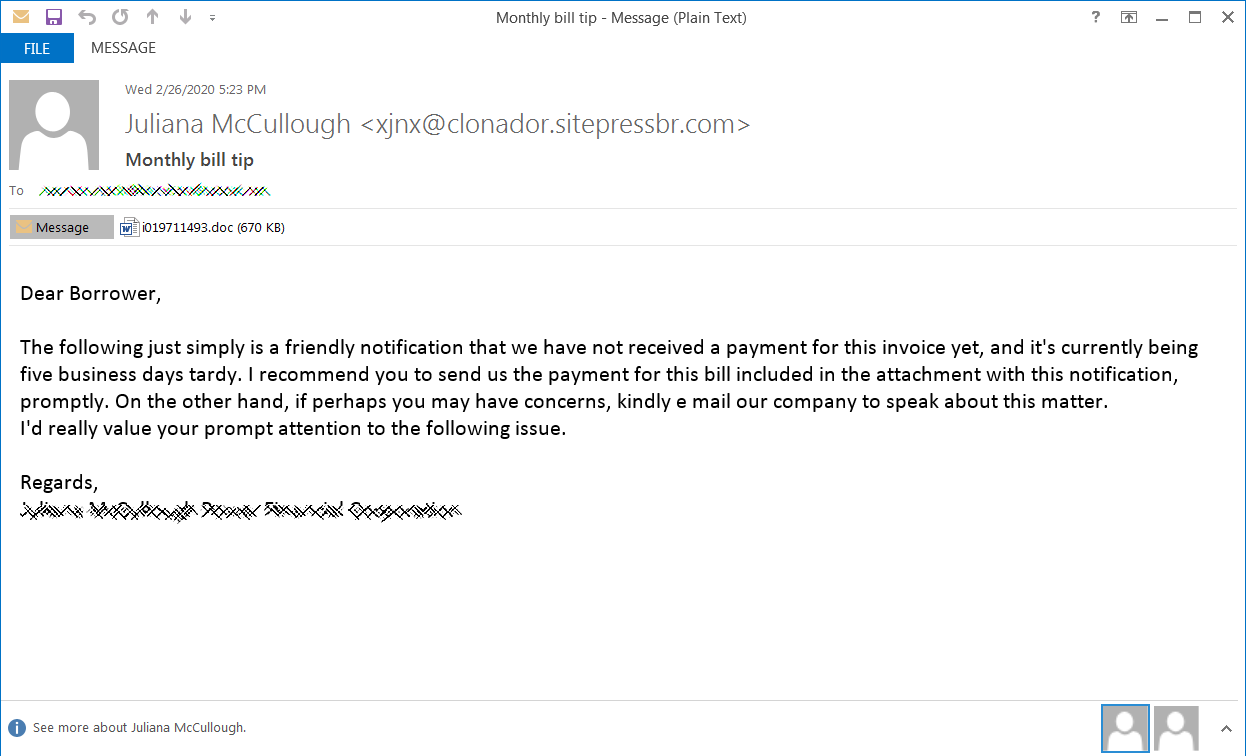
A phishing campaign is a prime source for any remote attacks. Here too, the attackers send phishing emails to potential victims with Word Documents and ask them to open it which contains malicious macros and images with encrypted content. Most commonly, the emails are sent asking for a missing payment and asking them to enable macros (which are turned off by default) to views the invoices in documents.
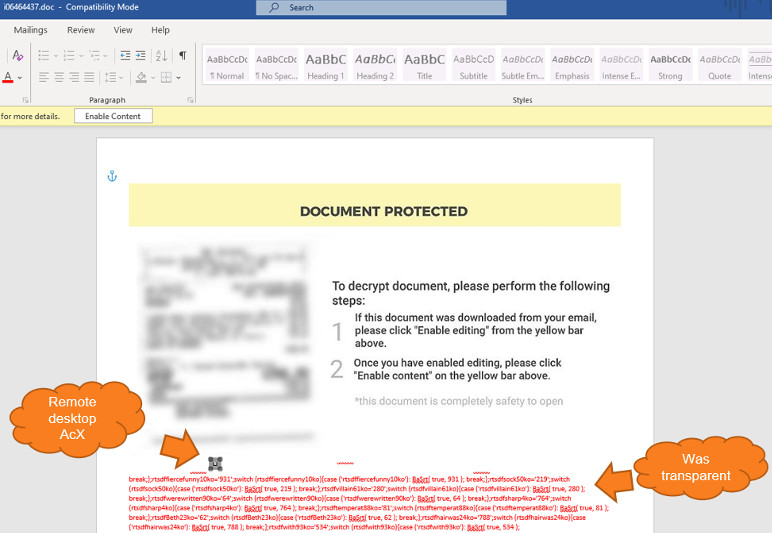
A deep look by Morphisec researchers revealed the image within the document containing ActiveX control, which is used for drawing layers in Word documents to make it more interactive. But here, the deeper analysis revealed the MsRdpClient10NotSafeForScripting class for controlling.
Tactics to Hide!
Attackers have long used many techniques to evade detection by flagging softwares, but here, the bunch used ActiveX control to dump and execute Ostap within Word document, that too making it invisible by executing it as the same colour as the background.
Further, they did not populate the server field in MsRdpClient10NotSafeForScripting class, so that they can use it for future exploitation. Within a macro, the OnDisconnected function is used as a trigger and form a backdoor for taking in a .BAT file. Speaking of this campaign, Michael Gorelik from Morphisec said, “The OSTAP will not execute unless the error number matches exactly to disconnectReasonDNSLookupFailed (260); the OSTAP wscript command is concatenated with a combination of characters that are dependent on the error number calculation.” Via: Bleeping Computer